Technology
How Spearphishing Works and How You Can Catch It

Cybercriminals are constantly evolving their methods, and spearphishing is one of the most deceptive tactics in their arsenal.
These attacks can be difficult to spot, as they often appear to come from someone you know and trust, like a colleague or business partner.
What is Spearphishing?
Spearphishing is one of the most targeted forms of phishing attacks. Unlike regular phishing, where attackers send mass emails to random users, spearphishing is highly focused on specific individuals or organizations. These attacks often come disguised as legitimate communication, making them harder to detect.
The goal of a spearphishing attack is to trick the recipient into revealing sensitive information, such as login credentials or financial details, or to execute malicious software by opening a link or file attachment. Attackers invest time in crafting their messages to appear trustworthy, increasing the chance of success.
Key techniques attackers use for spearphishing:
- Email spoofing: Attackers send emails that look like they’re from someone you know by slightly changing the sender’s address.
- Malicious attachments: The email might include a file (like a document or PDF) that contains harmful software when you open it.
- Phishing links: They provide links that seem legitimate but lead to fake websites or downloading malware.
- Social engineering: Attackers learn details about you from social media or other sources to make their messages more convincing.
- Urgent requests: They pressure you to take quick action, like updating your password or paying a bill immediately, so you don’t think it through.
- Credential harvesting: The goal is to get you to enter your login details on a fake site so they can steal your information.
Detecting a Real-World Spearphishing Attack
Because spearphishing attacks are highly targeted, they can be very hard to spot. Even if an email looks like it’s from someone familiar, like a colleague, it might actually be a carefully crafted spearphishing attempt. Just seeing a familiar name in your inbox doesn’t mean the message is legitimate—it could be part of a well-planned attack.
To understand how these attacks work, let’s look at a real-world example. Using a tool like ANY.RUN’s sandbox, which provides a secure, isolated environment, we can safely investigate suspicious emails and attachments without risking harm to our systems.
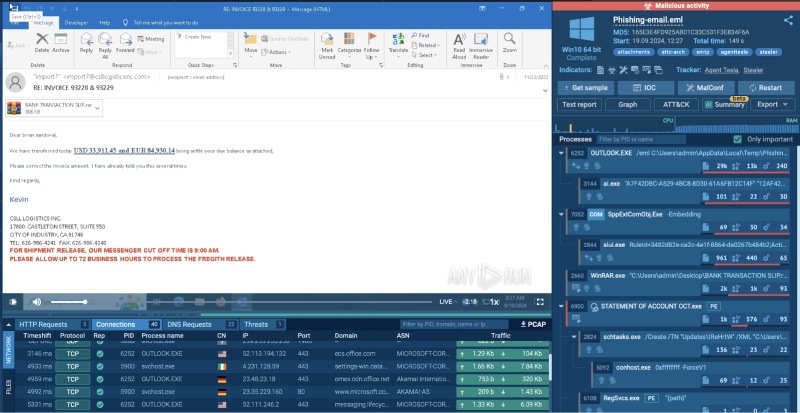
In this example, we received a suspicious email claiming that a payment had been made. The attacker wrote that the recipient had made a mistake in the invoice, asking them to check the attached document and correct the amount.
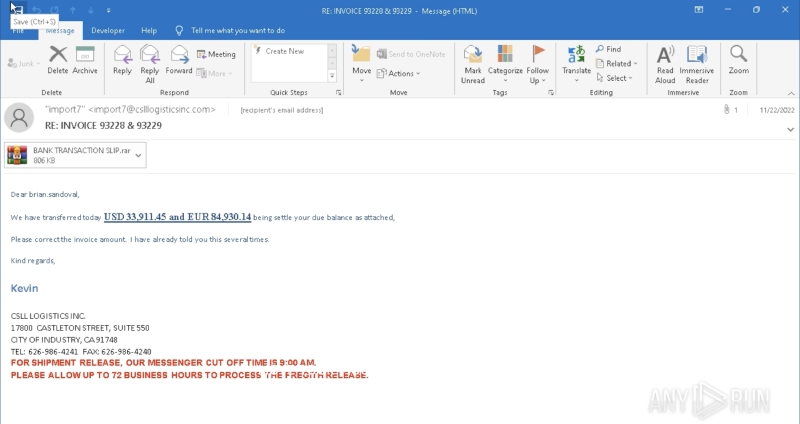
This tactic is designed to create urgency, pushing the recipient to act quickly without double-checking the email’s authenticity.
Using the ANY.RUN sandbox, we download the attached file to see what it really is.
Inside the archive, there’s a file named “STATEMENT OF ACCOUNT”—a tactic cybercriminals use to disguise harmful files with names that sound legitimate. In this case, the file is an executable, which is uncommon for typical business communications.
With the sandbox, we can safely open this file and watch what happens. As soon as it’s launched, the sandbox detects malicious activity.
The system confirms that the computer has been infected with Agent Tesla, a type of malware that allows attackers to steal sensitive information and spy on the victim’s activity.
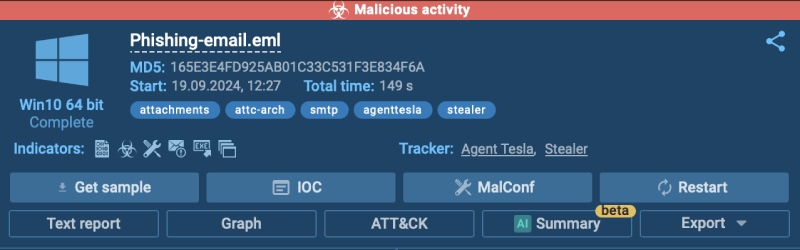
How a Sandbox Can Help Analyze Phishing and Malware
One of the easiest ways to avoid falling victim to spearphishing attacks is to analyze suspicious files, emails, and links in a sandbox environment. A sandbox allows you to safely open and execute potentially dangerous files or URLs without putting your device or data at risk.
Simply upload the suspicious file or copy and paste the URL inside the sandbox and see how safe or dangerous it is to open it on your real computer.
Technology
Fapelli: The Future of Digital Systems in 2025

Introduction to Fapelli
Fapelli is revolutionizing the technology industry. With over 50 million active users every month, this platform utilizes Artificial Intelligence (AI), Machine Learning, and Cloud Computing to provide cutting-edge digital solutions across industries such as retail, healthcare, finance, and education.
One of Fapelli’s biggest advantages is its ability to enhance business efficiency. A logistics company reduced its delivery time by 30%, while a tech startup saw a 40% increase in productivity. The success of this platform is driven by its AI-powered algorithms that analyze user behavior, blockchain technology that strengthens security, and predictive analytics that optimize inventory and trend forecasting.
In this article, we explore how Fapelli is setting new digital standards with a focus on security, privacy, and seamless integration.
The Journey of Fapelli (2023-2025)
Origin and Evolution
Fapelli was founded by a team of tech experts who aimed to develop innovative solutions that were both powerful and user-friendly. Their goal was not just to create another tech product but to build a platform that made technology accessible and intuitive.
Initially, Fapelli’s developers focused on user experience and content sharing. Their objective was to make technology so simple that users could perform their tasks effortlessly.
What set Fapelli apart was its user-first approach. While other companies prioritized technical specifications, Fapelli focused on enhancing user experience.
Feedback from users played a crucial role in its development. By continuously improving the platform based on user suggestions, a simple digital idea evolved into a comprehensive system serving multiple industries.
Key Milestones in Fapelli’s Growth
Between 2023 and 2024, Fapelli achieved several important milestones. The integration of AI, Cloud Computing, and the Internet of Things (IoT) transformed it into a powerful and user-friendly platform.
Key Features of Fapelli
- Customizable Dashboard – Users can personalize their workspace according to their needs.
- Multi-Device Optimization – Fapelli seamlessly operates across mobiles, tablets, and desktops.
- Advanced Security – With encryption and security protocols, data remains protected.
- User Feedback Program – Fapelli regularly incorporates feedback from its community to improve its platform.
By 2024, Fapelli had established itself as a major player in the digital industry. Its seamless experience and multi-device integration made it one of the most user-friendly platforms available.
The Future of Fapelli in 2025 and Beyond
Fapelli is not stopping here. In the future, the company plans to explore Virtual Reality (VR) and high-resolution streaming, making technology even more efficient while maintaining a focus on environmental responsibility.
If Fapelli continues on this trajectory, its user base is expected to double soon. The platform’s AI-powered innovations make it an essential tool for businesses and individuals alike.
Environment-Friendly Technology
Fapelli is also committed to developing eco-friendly products. With rising environmental concerns, people are looking for sustainable solutions. Fapelli is working on new materials that will make technology both sustainable and efficient.
Transforming the Financial Services Industry
Fapelli is bringing a digital revolution to the financial sector. Traditional banking models are becoming outdated, and financial institutions need advanced digital solutions.
Automated Risk Assessment
Risk assessment is one of the biggest challenges in the financial sector. Fapelli’s automated risk assessment tool makes this process easier and more accurate. By analyzing financial data in real-time, it generates risk metrics that help in better decision-making.
Benefits:
- Consistent Risk Analysis – Ensures risk is assessed using a uniform standard.
- Early Issue Detection – Predicts potential risks before they become major problems.
- Simplified Monitoring – Managers can track risk assessment from anywhere.
Fraud Detection System
Fraud is a major concern in banking and finance. Every year, companies lose millions due to fraudulent activities. Fapelli’s fraud detection system monitors live transactions and instantly detects any suspicious activities.
According to research, 33% of financial institutions are already using AI-based fraud detection, while another 31% plan to implement it in the coming years.
Benefits of Fapelli’s Fraud Detection System:
- Higher Accuracy – AI algorithms detect fraud with precision.
- Reduced Financial Losses – Early fraud detection helps prevent major financial losses.
- Increased Customer Trust – Enhanced security measures improve user confidence.
- Regulatory Compliance – Quickly detects suspicious activities, ensuring compliance with regulations.
Fapelli continuously monitors user behavior, and any unusual activity triggers an instant alert, making financial systems safer.
Conclusion
Fapelli is setting new standards in the digital world. Its focus on AI, security, and user experience makes it a powerful and reliable platform.
In the coming years, Fapelli will continue to innovate, whether through AI-powered applications, VR technology, or eco-friendly initiatives. The company’s vision is to make technology more accessible, efficient, and sustainable.
The Future of Fapelli
Beyond 2025, Fapelli will keep exploring new ways to enhance technology and improve user experience, making digital solutions simpler and more effective for everyone.
Technology
Blooket Login: A Simple and Easy Guide
If you’re looking for a fun way to learn and play educational games, Blooket is a great platform. But before you can start enjoying its exciting quizzes and challenges, you need to log in. In this guide, I’ll walk you through the Blooket login process in a simple and easy-to-understand way.
Whether you’re a student, teacher, or just someone who loves trivia games, this article will help you log in without any confusion. Let’s get started.
What is Blooket?
Blooket is an online learning platform where students can play quiz-based games created by teachers or other users. It makes learning fun, interactive, and engaging. The best part? You earn points and rewards while answering questions.
Blooket is commonly used in schools, but anyone can join and play. To get started, you need an account, and that’s where the login process comes in.
How to Log In to Blooket?
Logging in to Blooket is very easy. Just follow these simple steps:
Step 1: Open the Blooket Website
First, open your web browser and go to the official Blooket website:
Once the website loads, you’ll see a “Log In” button at the top right corner.
Step 2: Click on the “Log In” Button
Click on the “Log In” button. This will take you to the Blooket login page, where you’ll need to enter your credentials.
Step 3: Enter Your Login Details
Now, you need to enter your username or email and password. If you have already created an account, type in your details and click “Log In”.
Forgot your password? No worries. Click on “Forgot Password?” and follow the instructions to reset it.
Step 4: You’re Logged In
Once you enter the correct details, you’ll be redirected to your Blooket dashboard, where you can start playing games, joining quizzes, or creating your own game sessions.
That’s it. You’re now logged in to Blooket.
How to Log In with Google Account?
If you don’t want to remember another password, you can log in using your Google account. Here’s how:
- Go to www.blooket.com.
- Click on “Log In” at the top right.
- Choose “Log in with Google” instead of entering an email and password.
- Select your Google account.
- You’re in.
Logging in with Google is quick, easy, and secure.
How to Log In as a Teacher?
If you’re a teacher, the login process is the same. However, after logging in, you’ll get access to special features like:
- Creating custom quizzes
- Tracking student progress
- Hosting live Blooket games
Simply log in using your email and password or Google account, and you’re ready to make learning fun for your students.
How to Log In as a Student?
If you’re a student, you have two options:
- Log in with your account (if your teacher has asked you to create one).
- Join a game without logging in by entering the Game Code shared by your teacher.
For the best experience, it’s recommended to create an account so you can track your progress and earn rewards.
Common Login Problems and Solutions
Sometimes, you might face issues while logging in. Here’s how to fix them:
Problem 1: Forgot Password
Solution: Click on “Forgot Password?” and follow the steps to reset it.
Problem 2: Wrong Email or Password
Solution: Double-check your email and password for any typing mistakes.
Problem 3: Google Login Not Working
Solution: Try refreshing the page and logging in again. Make sure your Google account is active.
Problem 4: Website Not Loading
Solution: Check your internet connection or try using a different browser.
If none of these solutions work, visit Blooket’s Help Center for more support.
How to Stay Logged In
If you use Blooket regularly, you don’t want to log in every time. Here’s how you can stay logged in:
- Check the “Remember Me” box while logging in.
- Don’t clear cookies from your browser.
- Use the same device whenever you play.
This way, Blooket will keep you logged in automatically.
Final Words
Blooket is an amazing way to learn and play at the same time. Logging in is super easy, whether you’re a student, teacher, or just a game lover. Just follow the steps above, and you’ll be inside your account in no time.
Now that you know how to log in, go ahead and start playing exciting quizzes on Blooket.
Happy learning.
Technology
How to Use Janitor AI: A Simple and Easy Guide
Janitor is an innovative chatbot platform that allows users to create and interact with virtual characters. Whether you’re looking for a virtual assistant, a fun chatbot to chat with, or a role-playing companion, Janitor has something for everyone. This guide will walk you through everything you need to know about using Janitor in a simple and easy-to-understand manner.
What is Janitor?
Janitor is a chatbot platform that enables users to create, customize, and interact with virtual characters. These characters can have unique personalities, backgrounds, and behaviors, making interactions feel more personalized and engaging. Some common uses of Janitor include:
- Casual conversations
- Role-playing (RP)
- Customer support automation
- Creative storytelling
- Educational assistance
Unlike traditional chatbots that follow scripted responses, Janitor utilizes advanced technology to generate human-like responses based on the information it has been provided.
Getting Started with Janitor
Step 1: Creating an Account
Before you can use Janitor, you need to create an account. Follow these steps:
- Go to the Official Website: Open your web browser and visit the Janitor website.
- Sign Up: Click on the “Sign Up” button and enter your email address, username, and password.
- Verify Your Email: Check your email for a verification link and click on it to activate your account.
- Log In: Once verified, log into your Janitor account.
Step 2: Setting Up Your Profile
After signing up, you can customize your profile:
- Upload a profile picture
- Set a display name
- Adjust your preferences for chatbot interactions
This helps tailor your experience and ensures that the responses align with your preferences
Exploring and Using Characters
Step 3: Browsing Characters
Janitor provides various characters created by users. To find a chatbot you want to interact with:
- Click on the “Browse Characters” option.
- Use the search bar to look for characters based on name, tags, or personality traits.
- Click on a character’s profile to read its description and details.
- If you like the character, click “Chat” to start a conversation.
Step 4: Chatting with a Character
Once you’ve chosen a character:
- Type a message in the chatbox.
- Press Enter to send your message.
- The system will generate a response based on the character’s personality and training.
- Continue the conversation as long as you like.
Each character has a unique way of interacting based on how it was designed. Some characters may be more formal, while others might be more casual or playful.
Creating Your Own Character
One of the most exciting features of Janitor is the ability to create your own chatbot. Here’s how:
Step 5: Character Creation
- Go to “Create Character”: Click on the “Create” button in your dashboard.
- Enter Character Details:
- Name: Choose a unique name for your character.
- Avatar: Upload an image to represent your character.
- Description: Write a short bio explaining your character’s personality and purpose.
- Tags: Add tags like “friendly,” “funny,” or “professional” to categorize your character.
- Name: Choose a unique name for your character.
- Set Default Greetings: Write an opening message your character will send to users.
- Save & Publish: Click “Save” to finalize your character.
Once created, other users can find and chat with your character if you set it to public.
Advanced Features & Settings
Janitor allows users to configure settings to improve their experience. Here are some features you might find useful:
Step 6: Adjusting Personality & Behavior
- Adjust Response Style: You can tweak how formal, casual, or humorous your character should be.
- Set Memory Retention: Some models can remember past interactions, making conversations more natural.
- Enable Filters: You can control what types of conversations your character can engage in.
Step 7: API Integration (Optional)
For developers and businesses, Janitor offers API integration for embedding chatbots into websites or applications. If you want to use Janitor with an external model, you will need to:
- Get an API Key: Sign up for the API service you want to use.
- Enter the API Key: In Janitor’s settings, find the API integration section and enter your key.
- Save & Test: Make sure to save your changes and test the chatbot’s responses.
Common Issues and Troubleshooting
Even though Janitor is user-friendly, you might run into some common issues:
Problem 1: System Not Responding
- Check your internet connection.
- Refresh the page and try again.
- Ensure that the character is available for chatting.
Problem 2: Responses Are Repetitive
- Try rephrasing your messages.
- Use different characters for variety.
- Adjust the settings for a more dynamic conversation.
Problem 3: API Not Working
- Verify that the API key is entered correctly.
- Ensure the API service is active.
- Contact customer support if the issue persists.
Is Janitor Free?
Yes! Janitor offers a free version with its own built-in model. However, if you want to use more advanced models, you may need to subscribe to a paid plan.
Free vs Paid Features
| Feature | Free Plan | Paid Plan |
| Basic Chat | ✔ | ✔ |
| Custom Character Creation | ✔ | ✔ |
| Advanced Models | ✘ | ✔ |
| API Access | ✘ | ✔ |
| Priority Support | ✘ | ✔ |
Final Thoughts
Janitor is a powerful platform for anyone interested in chatbot technology. Whether you want to chat with a virtual assistant, create your own chatbot, or integrate conversational models into your business, Janitor makes it easy to do so. Follow the steps in this guide to get started and explore the endless possibilities of chatbot interactions!
-

 Entertainment11 months ago
Entertainment11 months agoBest Kickass Proxy List 2024 – 100% Working to Unblock to Access
-

 Lifestyle11 months ago
Lifestyle11 months agoBanging The Underdog Incident 2022
-

 Entertainment11 months ago
Entertainment11 months agoTamilMV Proxy Sites List 2025 – How to Unblock TamilMV Safely?
-

 Entertainment11 months ago
Entertainment11 months agoTamilRockers Proxy 2025: 20+ Working Links, Mirror Sites & VPN Guide
-

 Fashion9 months ago
Fashion9 months agoTrendy Midi Dresses for Casual Wear: Hair Care Tips Included!
-

 Entertainment11 months ago
Entertainment11 months agoPirate Bay Proxy List 2025: Access The Pirate Bay Safely
-

 Technology7 months ago
Technology7 months agoSSIS 469 – Detailed Guide to Understand The Features and Benefits
-

 Blog9 months ago
Blog9 months agoCy Kass – Family Detail of Alex Wagner and Sam Kass






